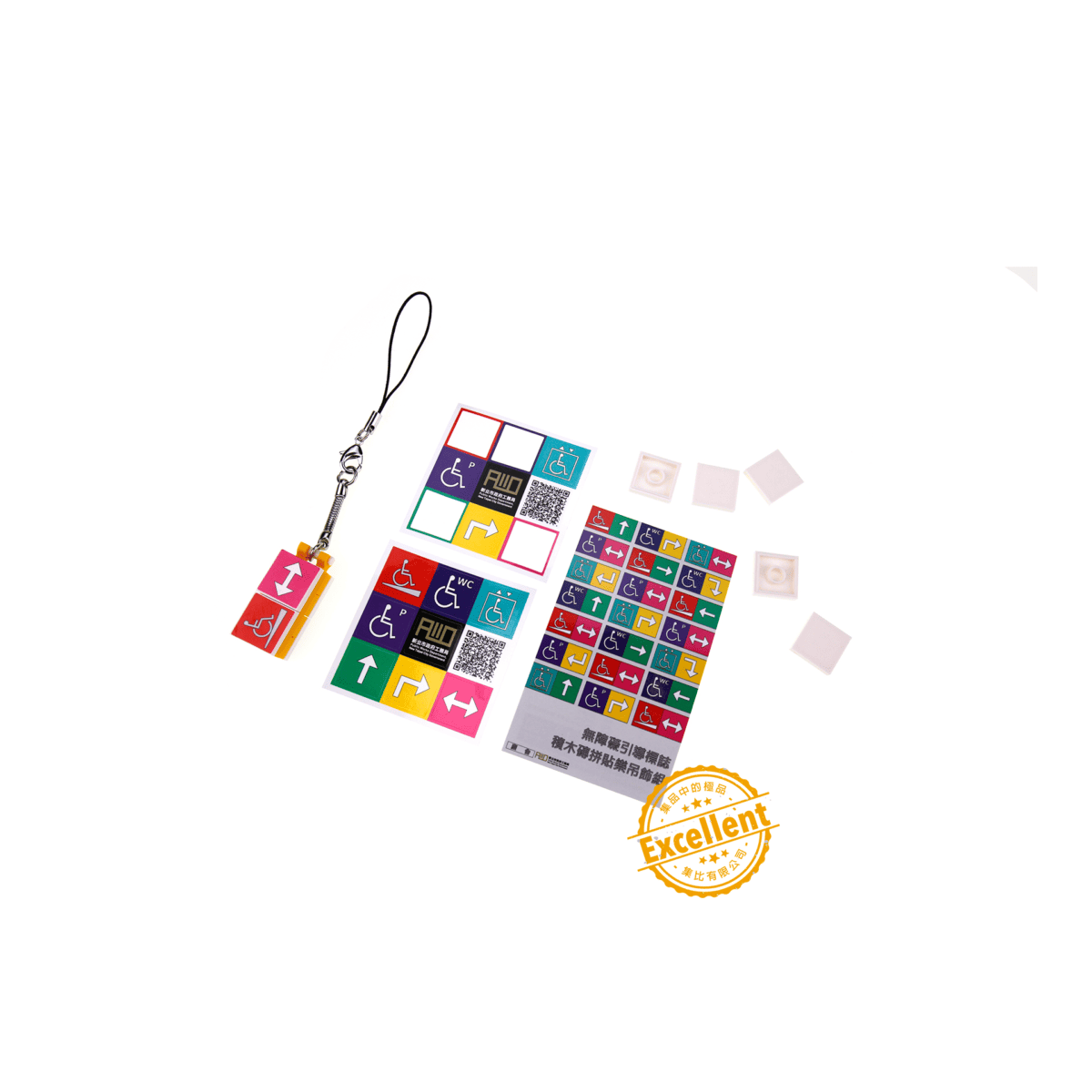
【穩固基礎 維護安全】城市的進步來自每一塊積木!新北市工務局訂製無障礙引導標誌積木磚拼貼樂吊飾組
這次和集比合作的主人公非常特別ーーー新北市工務局。相信很多民眾對工務局的業務掌管範圍不是很清楚,甚至不曉得市政 … 閱讀全文
【台南賞花景點】四月賞花何處去?美照去這裡拍就對了!賞花也要愛地球 客製化環保餐具推薦
萬物復甦的春天,把握花期一賞美景,無疑是人生中一大享受! 這次春遊來造訪美食之都台南吧!不僅大飽口福,也是盛大 … 閱讀全文
迴紋針是誰發明的?把迴紋針配戴在身上可能會被逮捕?關於迴紋針你不能不知道的3件事!
書桌上看似不起眼的小士兵──迴紋針,已經將近160歲了!迴紋針並非一開始就長成如今我們常見的樣貌,曾歷經不同形 … 閱讀全文
隨身碟中毒?檔案被刪光有救嗎?電腦視窗請你格式化隨身碟的3大原因報你知—客製化隨身碟推薦
隨身碟在資料傳輸上扮演極為重要的角色,與現代人的生活密不可分,是非常便利的工具。然而,您是否也曾遇過電腦跳出視 … 閱讀全文
被一成不變的生活壓得快喘不過去了嗎?快戴上屬於你的客製化行李吊牌替自己安排一場治癒的旅行吧!
在現代社會中,「玩樂」是一件需要被重新定義的事! 隨著生活節奏的加快和工作壓力的增加,許多人面臨著壓力和焦慮的 … 閱讀全文
不鏽鋼會生鏽嗎?如何清潔與保存不鏽鋼餐具?三個生活中一定要知道的不鏽鋼環保餐具知識
環境保護是眾所矚目的議題,使用環保餐具的人愈來愈多,環保餐具的材質也成了大家關注的焦點。麥稈、矽膠材質以及不鏽 … 閱讀全文